While my content is normally geared towards a corporate security audience about cyber vulnerabilities and endpoint security, a recent fraud perpetrated on a friend has made me realize that many of the scams targeting everyday users are not common knowledge. Although I was not the target, I feel affected. Since I know about how these scams generally work, I decided to compile these in the hopes that it can help at least one person avoid the sleepless nights and feelings of vulnerability that come with being tricked out of your hard-earned money.
There are thousands of such scams. As such this is not even close to being a complete list. It’s only a small sampling of some of the scams I’ve seen, read about or been targeted by.
Computer Scams:
Do NOT click on links in emails or even in text messages:
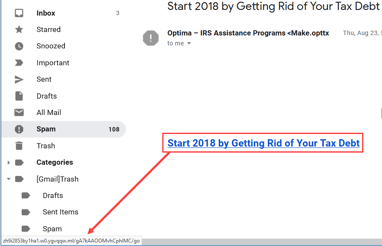
One of the ways hackers get to you is by making you come to them. They send you an email with a link that you must click on to “claim your prize” or “reschedule delivery of a package”. Although the title of this link may say www.fedex.com or www.ups.com it will most definitely not take you to that website.
You can verify the authenticity of the link by hovering over it with your mouse (but do not click) and look somewhere on the bottom of the page. You will see a URL appear that will usually tell you the real destination of the link. Better yet, don’t click on any links in any email that you were not specifically waiting for.
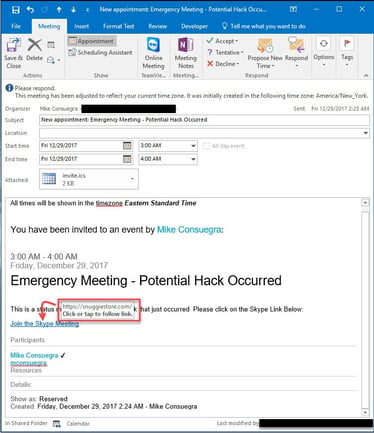
Do NOT click on links in a calendar entry you don’t recognize:
This one falls into the same category as the previous point. Unknown web-links are ‘bear traps’. In some cases, hackers that can’t get past your spam filters send calendar invites to your email address with malicious links disguised as benign ones. It may be tempting to click on these because they are in our calendars, but same rules apply to calendar entries: Do not click on any unless you are sure exactly where they will lead.
Do NOT insert a USB stick you found into your computer:

Finding a USB stick in the parking lot is not like finding a $100 bill on the street. In fact, it might be the complete opposite in that using it will likely cost you money, among other things.
It’s an old trick, but hackers can often load a USB stick with malware and tempt you to install it by giving salacious names to files like: ‘executive_bonus.zip’ or ‘confidential.pdf’. As soon as you click the file, the malware installs, and you’re Done. Don’t make it easy for them.
Be wary when connecting to public hotspots:
 Remember that one time you used the Wi-Fi at a hotel or coffee shop? Your device does! Your laptop, tablet or phone will usually store a Wi-Fi hotspot’s SSID after you’ve connected to it. Some devices have the option “connect to known networks” enabled by default. This means that the next time you come within distance of that network your device will automatically connect to it. That’s a great convenience if it weren’t for hackers. Bad actors can use a device such as a WiFi Pineapple Router to clone and mimic common WiFi hotspot SSIDs. If you come within distance of this device while sitting at a café or walking through the mall your device will automatically connect to their hotspot and they can see everything you’re doing. Since their router can also serve out internet access you will even be able to browse the web while connected to this fake hotspot, but everything you are doing on the web is being monitored (web logins, emails, etc.). So the next time you are sitting at a Starbucks in a mall in Boise, Idaho think about why your device is connected to the “Boston Logan WiFi network”.
Remember that one time you used the Wi-Fi at a hotel or coffee shop? Your device does! Your laptop, tablet or phone will usually store a Wi-Fi hotspot’s SSID after you’ve connected to it. Some devices have the option “connect to known networks” enabled by default. This means that the next time you come within distance of that network your device will automatically connect to it. That’s a great convenience if it weren’t for hackers. Bad actors can use a device such as a WiFi Pineapple Router to clone and mimic common WiFi hotspot SSIDs. If you come within distance of this device while sitting at a café or walking through the mall your device will automatically connect to their hotspot and they can see everything you’re doing. Since their router can also serve out internet access you will even be able to browse the web while connected to this fake hotspot, but everything you are doing on the web is being monitored (web logins, emails, etc.). So the next time you are sitting at a Starbucks in a mall in Boise, Idaho think about why your device is connected to the “Boston Logan WiFi network”.
The most effective way to avoid this is to “Forget” the network when you are done using it. This is one of the options in your Wi-Fi settings. By telling your device to “Forget this Network” it forces you to manually select the network you want to connect to in the future. This doesn’t mean you won’t still choose that bad hotspot if you’re fooled into thinking it’s legit. You must be on the lookout and think about whether it makes sense to see that hotspot in your location. As an alternative to the step above you can just turn off your Wi-Fi all together when you are out and about. Most people have data plans so it’s not like you actually need a Wi-Fi connection to use your phone while out in public.
Phone Scams:
The IRS is NOT calling you despite whatever the caller ID says
This is one that people keep falling for even though it has been ongoing for several years and the IRS warns people about it every year. The caller pretends to be from the IRS and tells you that they have an arrest order and the police will be on their way unless you pay some random amount that you ‘owe on back taxes’. This scam is easily defeated by simply calling your accountant to verify what they’re telling you. The problem is that these fake ‘IRS’ agents tell you that if you don’t stay on the phone continuously until you pay the money the cops will be on their way.
 They further tell you that you must not talk to anyone else about this and that you must make the payment in Bitcoin, an anonymous, hard to trace and virtually impossible to recover cryptocurrency. On its face, it’s hard to imagine how people could fall for this scam since the story you are being told is so ridiculous. Comedian James Veitch has made a name for himself interacting with scam email authors and he put it best this way:
They further tell you that you must not talk to anyone else about this and that you must make the payment in Bitcoin, an anonymous, hard to trace and virtually impossible to recover cryptocurrency. On its face, it’s hard to imagine how people could fall for this scam since the story you are being told is so ridiculous. Comedian James Veitch has made a name for himself interacting with scam email authors and he put it best this way:
“By making the scams ridiculous, ideally for the scammers, the only people who are going to reply are the most gullible people.”
This is the same case with the phone calls. Out of 1,000 calls they make 950 people will likely hang up, but they realize that the 50 that stay on and interact with them are the most likely to believe what they are being told and send them money. Understand this: the IRS will never demand money over the phone and they will most certainly not demand that you pay it in bitcoin without talking to anyone else first. The next time you get this call, just hang up.
Microsoft Tech Support is NOT calling you and asking for money or personal details:
There are variations of this scam in which a fraudster will call you and tell you that they have received a message from your computer that it has viruses. Generally, they will then ask you to visit some webpage or download some utility that will allow them to see/control your computer. In case it’s not obvious by that point: Don’t do any of this!
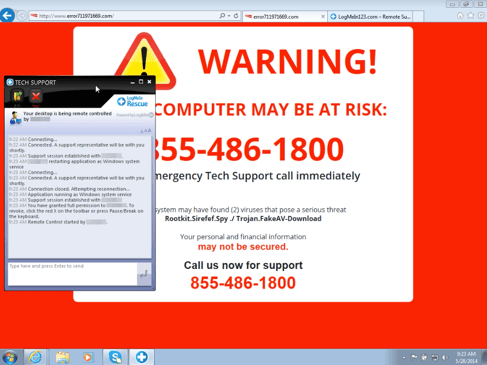
In the most benign versions of this scam you will be tricked into paying for a ‘clean-up’ service or ‘virus removal’ that they say they have just performed. In the most malign version they will put malware on your computer that can be used to steal information/money from you. When in doubt ask for their name and what company they are calling from. Then promptly search for the company, visit their actual website and call the customer service number listed there. If you tell the scammer you are going to do this, they will try to dissuade you from it by telling you that if you don’t resolve this with them right-away you will be sued or other such nonsense. Again, if it’s not obvious by that point: It’s a scam. Hang up!
Virtual kidnapping:
Most scams prey on our ignorance or fear. This is one that is particularly heinous and preys on the most frightening event that a parent could ever experience: the thought that their son or daughter has been kidnapped and is being held for ransom. The NIH has the best description of this scam:
The scam typically begins with a phone call saying your family member is being held captive. The caller may allege your daughter has been kidnapped and you hear a female screaming in the background. Another variant of the fraud has a family member being held because he/she caused an auto accident, is injured and won't be allowed to go to the hospital until damages are paid. Callers will typically provide the victim with specific instructions to ensure a safe return of the family member. You may be ordered to stay on the line until money is wired. The caller may claim not to have received the money and may demand more payment.
The first thing that you need to do when confronted with such a phone call is calm down. The caller will depend on the fact that such a call would unnerve anyone and keep them from thinking clearly. So, the first thing you must do is calm down so you can think clearly. At this point you can put your countermeasures into effect. You will find many of these in the NIH linked article above, but for simplicity I will list some here:
First, try to verify that they really have who they say they have:
a. Ask to speak with your relative to verify they are okay
b. Ask the caller to call you from your family member’s cellphone
c. Ask the caller to describe the person they have and tell you what they are wearing
d. Try to text or call the person from another line or via social media on your computer.
These are all good suggestions, but keep in mind that a practiced scammer might be able to give you good enough answers to convince you the situation is real.
- If the caller has seen the person from a distance or the victim’s social media accounts have recent pictures they may be able to guess at a description and clothing
- They may tell you that the person’s phone was lost or destroyed during the kidnapping
- They may tell you that the person is unconscious and can’t speak
Every person will respond differently to this type of call so there is no ‘one size fits all’ solution for dealing with it.
A suggestion that I have not seen in some of the advisories online relating to these types of calls is the you establish a “Family Emergency Password”. This word should be something that means absolutely nothing to anyone else except you and your family. It should be easy enough to remember even in a situation of high stress. You should emphasize to your family that they need to remember this password, but never divulge it to anyone except in situations where you need to prove to your family that you are speaking through a third party.
Because it is a single word it can be quickly spoken or written to verify the authenticity of the caller's claims. The only case in which this may not work is if the kidnapper says the victim sustained injuries, is unconscious and can’t be woken. At this point you may need to use your best judgement to determine if the caller is being truthful or if you still think it's a scam. Hopefully by this time you have had the opportunity to convey the situation to someone else and have them try to locate the victim via other means. When the safety of a family member is potentially at risk and it’s not just about a hacked computer or a possible identity theft, the decision to pay or not becomes deeply personal. It would be hard for someone else to give you advice in this instance, so I will defer to your own judgement.
Mail Scams:
Never Accept MORE than what you are owed on anything you are selling:
This is one that has been going on for years but is less common since the rise of online escrow services like PayPal. In general, the scam goes like this: You are selling something on an online marketplace. The buyer tells you that they will buy at your listed price, but they will pay you with a check (cashier’s, money order, etc.) that is made out in the buyer’s name and is for more money than the cost of the item you are selling. The catch is that the check they are sending you has a blank endorsement, which makes the check into a bearer instrument. Think check that has been made out to cash and endorsed. As defined by the United States UCC, article 3 any check that has been endorsed by the payee becomes a bearer instrument and can be cashed by anyone who “bears” or is in possession of it.
The buyer says that they just haven’t had time to deposit the ‘check’ and figures if you deposit it and collect the entire amount you can send them the difference between the price of your item and the amount they sent you. The real trouble comes in a week or two when your bank tells you that the cashier’s check or money order you deposited is fake or has been reported stolen. At that point, they debit your account for the entire amount. You lose the money you sold the item for, the item you undoubtedly already shipped and the difference between the price of the item and amount they sent you which you so honestly refunded them. The way I have avoided even being targeted by this scam is by putting the following disclaimer in any online forums where I post items for sale (if checks are an option for payment):
Warning: I will only accept payment of the exact amount of my item. If you send me a check for more than the asking price I am keeping the rest and will not ship the item out until 3 days after I have verified with the issuing bank that the check is good.
This usually weeds out most of the attempts. The bottom line: In this age of instant payment systems accepting a check for an item sold online is risky. If you do, however, don’t ship anything out until you verify that the check you deposited was accepted by the issuing bank.
Official-looking Government Correspondence:
 As with other scams there are countless variations on this theme, but the general concept is that of receiving a letter that looks like it comes from the US Government or some other official agency and has words like “Final Notice” or “Expiration Notice”. Many of these are attempts to get you to send money in to “extend” your vehicle warranty or scare you into thinking you owe some money to the IRS or other state or Federal Agency.
As with other scams there are countless variations on this theme, but the general concept is that of receiving a letter that looks like it comes from the US Government or some other official agency and has words like “Final Notice” or “Expiration Notice”. Many of these are attempts to get you to send money in to “extend” your vehicle warranty or scare you into thinking you owe some money to the IRS or other state or Federal Agency.
Bear in mind that not all of these will be fake. If you forgot to pay something you may get an actual collection notice, but generally you will get a 1st, 2nd and maybe even a 3rd notice before you get a “Final” notice. The best thing to do if you have any doubt as to the letter’s authenticity is to see who it’s coming from. Look up the sender and call them at the number listed on their valid company web site, not at the number on the letter.
General Tips and Warnings:
Job offers from unknown individuals that come with a ‘processing fee’:
This is one that, sadly, becomes more prevalent during bad times. The scammers hope that the normal alarm bells that go off when you hear something incredible will be quieted by the desperation of finding a job in a bad economy. If you receive an unsolicited call or email offering you a job but asking that you pay an upfront fee for “training, processing, application fee, etc.” it is a scam. No legitimate company would charge a job applicant for applying to the job. This scam changes stripes but can often come in the form of a “work from home” position or even a job that requires no interview. Think about it this way: Even your local fast food restaurant will interview you at least once before offering you the job of flipping burgers. How likely is it that a job paying 50k or more a year will hire you sight unseen and un-interviewed? The way to stay safe from this one is easy: If it sounds too good to be true, it probably is.
Re-using email passwords in online-accounts:
When you create a web-based account for any online service you are often asked to provide your email address. This is either used as your user name for that website or just as a form of communication from that website. If your email is listed anywhere on this site (especially as the user id) don't use the same password for the account as you do for your email. As has been seen in many cases over the last few years not all websites protect user data (including passwords) as well as they should. As a result, if your data is stolen from this website then the hacker will already know your email address and may even know the password you are using for the breached site.
Bet your bottom dollar that the first thing the hacker will do is try to logon to your email account using the password you used on this site. If they are both the same, then you just multiplied your exposure exponentially. Even if you use the same password for multiple web accounts (still a terrible idea, but it happens) make sure that the password for your email account(s) are always different than the one you use on any other websites.
Buy a paper shredder and use it!
Anything that has your name along with an account number or other contact info can be used to initiate an attack against you. Before the age of email and big data hackers use to get data on their targets by “dumpster diving”. That is, going through your garbage looking for bits of Personally Identifiable Information that they could use to their advantage. Just because everything is “in the cloud” now-a-days don’t think that people won’t go through your garbage anymore. They will. The best way to stay safe from this type of attack is to buy a shredder. Keep in mind that there are different types of shredders that offer different levels of security. Here is a comparison between the least secure (straight cut), more secure (cross-cut) and most secure (strip-cut).

Shredders offer different levels of shredding ranging from ‘consumer’ all the way to ‘Top-Secret’. Regardless of which one you choose, some shredding is better than none at all.
This list is just a small sample of the many scams that you may run into while out in the wild. Just because you haven't seen all of these or any of these it doesn't mean you won't ever see them. So keep your eyes open and your wallets closed.
