IAM is still dominated by traditional legacy platforms within large enterprises. As it takes both a large amount of dollars and time to implement, the ability to respond to threats and business changes are difficult - taking months or years to implement them. With an alarming number of large identity breaches happening in 2017, IAM platforms cannot respond fast enough to the ever-changing threat landscape. This increases the importance of identity and access management and puts it at the forefront of an organization's cybersecurity defense strategy.
Besides threats in 2018, several new additions to the IT and security landscape will affect how we view, protect, and govern our identities.
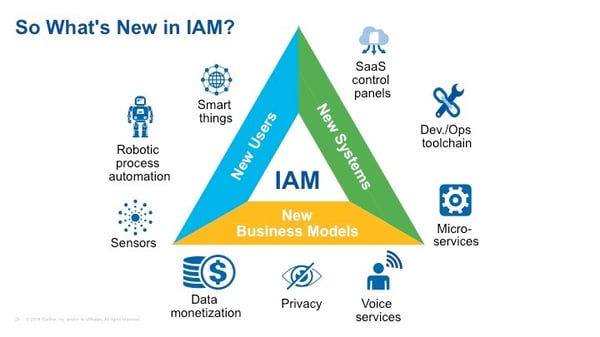
Gartner Event Presentation, State of Identity and Access Management 2018, Mary Ruddy, Gartner Security & Risk Management Summit, 04 – 07 June 2018 / National Harbor, MD
What are the changes that are affecting IAM in 2018?
Mary Ruddy’s presentation at the Gartner Secuirty Summit classifies these new additions in IAM as new users, new systems and new business models. As industry proffesionals, we can validate these new additions and add more detail.
- DevOps - DevOps is increasing in adoption in organizations. The goal is to provide methods for automated deployments, containerization of apps and servers and more importantly efficient methods for the merging of development, QA, and operations functions with an IT organization.
- The identity of things (IDoT) - This refers to the growing amount of internet connected devices. Everything from sensors, Voice devices(Alexa, Google home) Smart objects (Nest) must all be protected and are potential entry points to a breach. These all include an identity that must be managed and governed in the IAM/IGA stack.
- Privacy - The addition of GDPR in Europe has created the focus on how identities are stored and even removed from within an enterprise. The IAM/IGA stack must be able to respond to how external facing identities (i.e. customer metadata) is stored and secured.
- IAM Microservices - This is the breaking apart of large IAM stacks into smaller more manageable, scalable, and readily deployable Microservices. This architecture style has growing traction in the security space as it is a key method and driver for modernizing legacy IAM/IGA stacks.
The year of the IAM Microservice
Legacy IAM/IGA stacks are one of the largest causes of technical debt in IAM due to long implementation time and the inability to respond to changing requirements. In 2018, IAM Microservices are breaking down these legacy stacks into small and more lightweight services. The goal is to modernize IAM Programs and create a more service-oriented approach to IAM.
The use of a collection of IAM specific microservices (IAM Microservices) give us the ability to add IDot, automation, DevOps and new technologies, all while leveraging our existing technology investments and increasing deployment agility due to inherently supporting DevOps tooling.

Gartner Event Presentation, State of Identity and Access Management 2018, Mary Ruddy, Gartner Security & Risk Management Summit, 04 – 07 June 2018 / National Harbor, MD
How can organizations get started in their IAM modernization journey?
- Perform a robust IAM Advisory assessment to identify where you are, where you want to be, and how to get there. The main focus here is performing the assessment against a robust and modern IAM Program Reference Framework. The main outcome is an agile and nimble IAM Program Roadmap that identifies the highest risk cybersecurity, IAM, and IGA, gaps and takes immediate action to remediate. Learn more about how to get started with an IAM assessment.
- Implement modern IAM Services such as IAM Microservices to not only remediate immediate cybersecurity gaps, but also modernize the architecture and infrastructure at the same time. This will aid in the establishment of modern, robust, and nimble IAM capabilities for both on-premise and hybrid cloud systems. See www.perseusiam.com for more details regarding the world's first IAM Microservices platform.
- Establish a repeatable and measurable feedback loop to increase the maturity, effectiveness, and efficiency of the IAM Program over time.
About Aldo Pietropaolo
Aldo Pietropaolo is a cybersecurity evangelist, identity security expert, and co-founder of Good Dog Labs, A Lighthouse Company. Good Dog Labs, modernizes identity and access management and governance for SMB’s and large enterprises using advisory and implementation services in addition to bringing new innovative products such as Perseus IAM (www.perseusiam.com) to market.
Ready to modernize your IAM?
Learn more about an assessment!
